Australia Cybersecurity Market Outlook to 2030
By Offering (Solutions and Services), By Security Type (Network Security, Endpoint Security, Cloud Security, Application Security, Identity & Access Management, Data Security), By Deployment Mode (Cloud-based, On-premises, Hybrid), By Industry Verticals
- Product Code: TDR0220
- Region: Asia
- Published on: August 2025
- Total Pages: 80
Report Summary
The report title “Australia Cybersecurity Market Outlook to 2030 – By Offering (Solutions and Services), By Security Type (Network Security, Endpoint Security, Cloud Security, Application Security, Identity & Access Management, Data Security), By Deployment Mode (Cloud-based, On-premises, Hybrid), By Industry Verticals (Financial Services, Government & Defense, Healthcare, Energy & Utilities, Retail & E-commerce, and Others), By Organization Size (SMEs and Large Enterprises), and By Region (New South Wales, Victoria, Queensland, Western Australia, South Australia, Tasmania, Northern Territory, and Australian Capital Territory)” covers a detailed analysis of the Australia cybersecurity market, exploring its overview and genesis, evolution from early perimeter-based models to integrated, identity-first architectures, and adoption across key sectors. It presents the overall market size in terms of revenue and evaluates market segmentation by offering, security type, deployment mode, industry verticals, organization size, and region. The study examines macroeconomic enablers such as digital transformation intensity, regulatory obligations under the Security of Critical Infrastructure Act, Essential Eight maturity uplift, and the growing demand for sovereign cloud capabilities. The report concludes with forward-looking market projections by revenue, segment, and region to 2030, cause-and-effect analysis of macroeconomic and regulatory drivers, and success case studies highlighting notable cybersecurity uplift programs in Australia. It also identifies major opportunities, critical bottlenecks, and strategic recommendations for stakeholders across the cybersecurity ecosystem.
Australia Cybersecurity Market Overview and Size
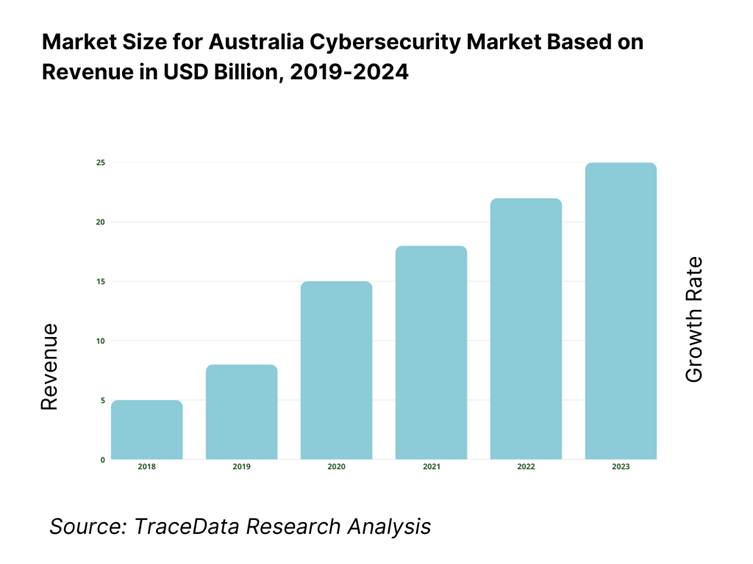
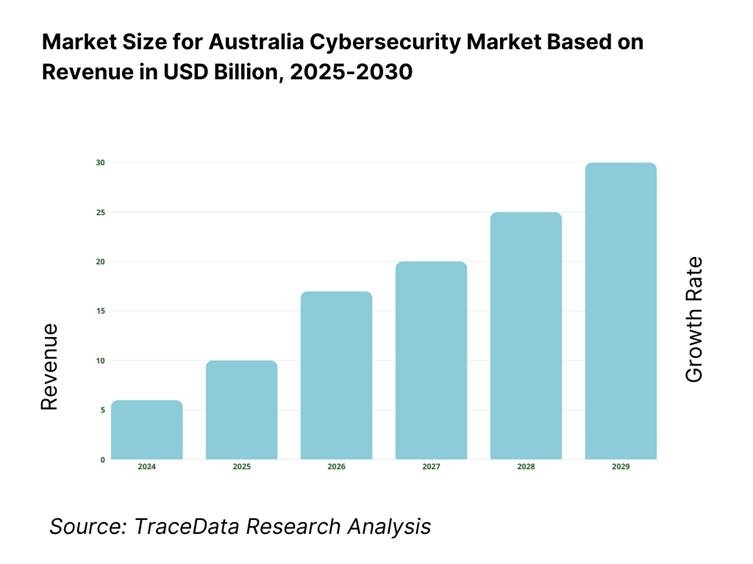
The Australia cybersecurity market stands at USD 5.8 billion, according to government-sourced projections based on 2024 data. Growth has been propelled by mounting digital threats, increasing regulatory pressures, elevated digital transformation across industries, and businesses consolidating digital strategies to mitigate heightened cyber risk.
Sydney and Melbourne lead the market, owing to their status as economic and technological hubs. Sydney's concentration of large corporations, financial institutions, and government agencies boosts demand for advanced cybersecurity solutions, while Melbourne’s thriving tech ecosystem and growing SME base drive adoption of innovative services.
What Factors are Leading to the Growth of the Australia Cybersecurity Market:
Critical infrastructure digitization: Regulation now covers 11 critical infrastructure sectors under the Security of Critical Infrastructure framework, formalising obligations for owners and operators. On the ground, electricity networks delivered 170,227 GWh through regulated transmission assets, and distribution served 10,953,197 customers across 767,798 km of lines—operations increasingly reliant on digital control and telemetry. Freight rail and related logistics datasets underscore digitised, interconnected assets across energy, transport and ports, reinforcing demand for ICS visibility, incident reporting and cyber-physical risk programs aligned to regulated sectors.
Privacy posture: Australia’s Notifiable Data Breaches scheme recorded 1,113 notifications in half-year reporting, evidencing the scale of personal and regulated data at risk. The commercial footprint includes 2,662,998 actively trading businesses, with 999,161 employing businesses that operate customer, payroll and supplier systems at scale. Payments intensity is high: RBA data shows 65.4 million cards on issue and 1,332.9 million monthly card purchases, amplifying requirements for data governance, breach response and identity assurance under privacy law. These volumes crystallise investment needs in DLP, encryption, identity proofing, breach readiness and third-party assurance.
Cyber insurance adoption: Macro exposure indicators point to strong risk transfer drivers. Australia hosts 999,161 employing businesses across finance, healthcare, retail and manufacturing—each operating payroll, payments and supplier systems—and 1,663,837 non-employing enterprises integrating SaaS tools. The RBA counted 65.4 million cards on issue and 1,332.9 million card purchases in a single month, while mobile services in operation reached 34,000,000, expanding digital entry points. With GDP at USD 1.77 trillion, enterprise and SME risk pools are large enough to justify broader cyber insurance uptake linked to controls like MFA, backups and incident response playbooks.
Which Industry Challenges Have Impacted the Growth of the Australia Cybersecurity Market:
Legacy tech debt: Large, long-lived infrastructure creates integration complexity with modern controls. Electricity distribution networks encompass 767,798 km of lines and 10,953,197 customers, much of it engineered for unidirectional flows and legacy protection schemes now interfacing with DER, BESS and smart meters. Transmission spans 43,885 km, and AEMO’s pipeline shows 2,090 km of new lines progressing, compelling staged upgrades to substations, SCADA and telecoms. This asset base forces layered security across diverse vintages, complicating patching, identity and segmentation for operational technology that cannot be readily replaced without service disruption.
Fragmented tooling: The sheer number of operating entities and endpoints fragments control planes. ABS lists 2,662,998 actively trading businesses (including 999,161 employing), each combining on-prem, SaaS and telco stacks. ACMA identifies around 50 MVNOs alongside major carriers, and 34,000,000 mobile services in operation introduce heterogeneous device and eSIM profiles. Payments rails recorded 65.4 million cards on issue and 1,332.9 million monthly purchases, multiplying identities, tokens and logs. This diversity leads to overlapping agents, dashboards and policies that strain SOCs and drive need for consolidation via identity-first architectures and XDR.
Compliance burden: Security and privacy obligations are expanding in scope and cadence. The SOCI framework covers 11 sectors, while OAIC logged 1,113 notifiable data breaches in a half-year period, underscoring reporting and response requirements. Within government, 148 entities participated in ASD’s Partnership Program under PSPF Direction 003-2024, increasing compliance activity for controls uplift. ACSC also issued new PROTECT publications and updated the Information Security Manual and Essential Eight, adding concrete tasks for governance and audit teams. These quantified obligations elevate the need for policy automation, evidence collection and third-party risk oversight.
What are the Regulations and Initiatives which have Governed the Market:
ACSC advisories: The ACSC expanded guidance and joint work products for defenders. In 2023–24 it published 19 joint advisories with international partners, updated the Information Security Manual quarterly and refreshed the Essential Eight maturity model, plus released 29 PROTECT publications. The annual threat report recorded 36,700 hotline calls and more than 1,100 cyber security incidents handled, demonstrating operational tempo behind advisory issuance. This corpus of actionable content supports uplift across identity hardening, patch prioritisation and incident readiness for Australian organisations.
JCSC collaboration: Joint Cyber Security Centres operate in five capital cities, giving businesses regional access to briefings, exercises and information sharing with ASD, state agencies and industry. Engagement volumes reflect demand: the Cyber Security Hotline fielded 36,700 calls in 2023–24, and agencies issued frequent alerts and workshops through these hubs. The distributed JCSC footprint aligns with Australia’s population of 27,204,809, enabling multi-jurisdictional outreach to critical sectors and SMEs that cannot centralise teams in Canberra.
Critical infrastructure uplift grants: The Critical Infrastructure Uplift Program (CI-UP) reported 10 uplifts completed covering 15 critical infrastructure assets, with 5 uplifts in progress, 17 uplift information packs issued and 42 workshops delivered. Separate Commonwealth resilience measures funded 386 regional telecom hardening projects in one round to strengthen mobile sites supporting emergency communications. These quantified interventions translate directly into cyber uplift for OT operators and regional carriers, with measurable activities organisations can align to their risk registers and board reporting.
Australia Cybersecurity Market Segmentation
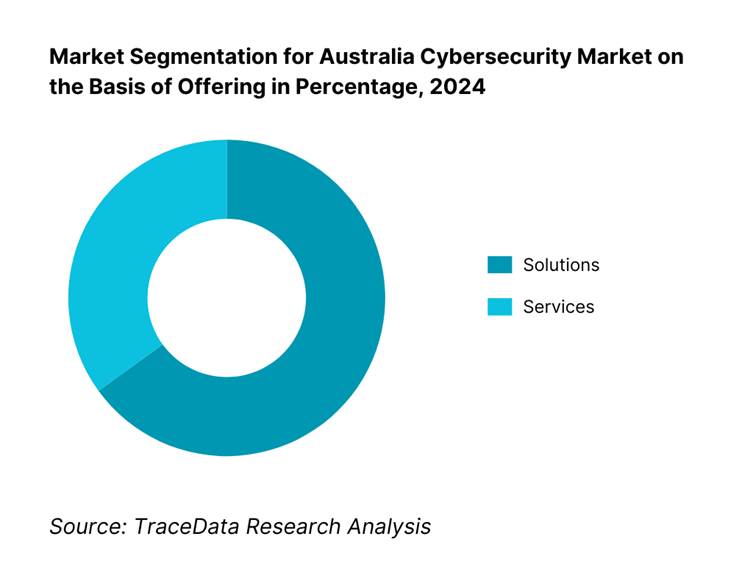
By Offering: The Australia cybersecurity market is segmented into solutions and services. Currently, solutions dominate, driven by increasing adoption of integrated security platforms offering comprehensive protection across endpoints, networks, and cloud. Businesses prioritize consolidating cybersecurity operations into unified solution suites to simplify complexity and maximize oversight.
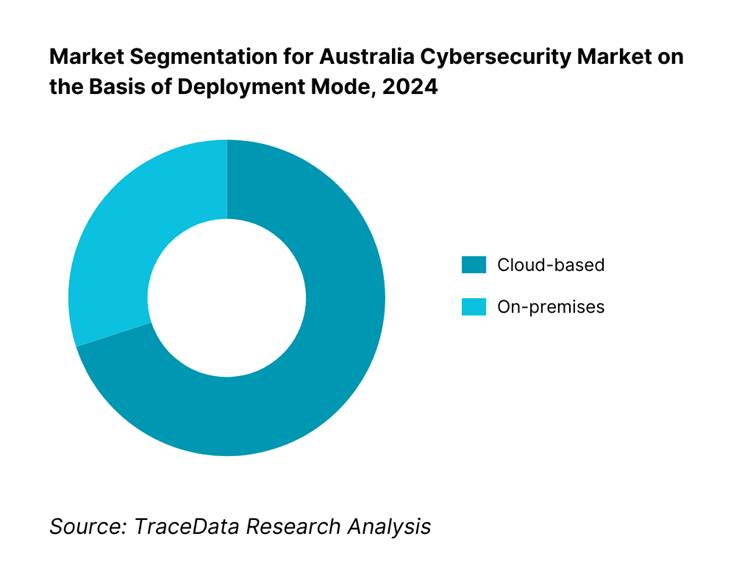
By Deployment Mode: The market is segmented into cloud-based and on‑premise deployments. Cloud-based solutions hold the dominant share, as Australian organizations increasingly migrate infrastructure and workloads to cloud for scalability, cost-effectiveness, and remote-readiness; this shift drives demand for adaptable, scalable cloud-native cybersecurity protections.
Competitive Landscape in Australia Cybersecurity Market
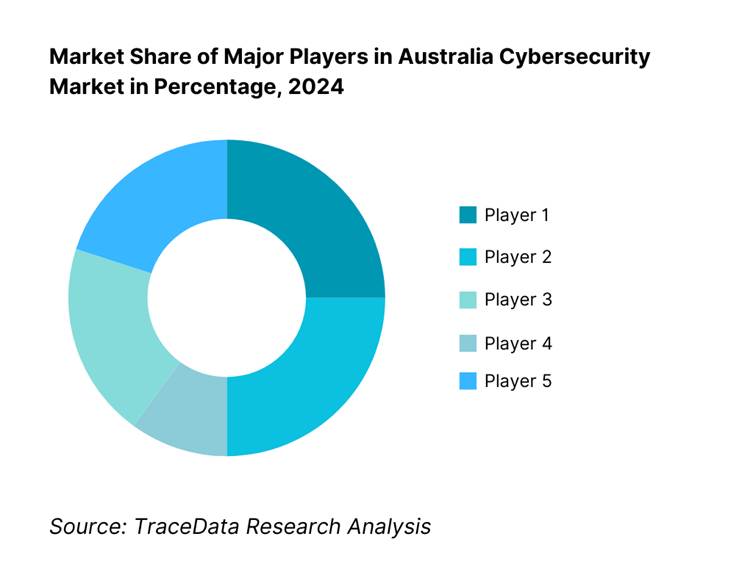
The Australia cybersecurity market is moderately concentrated, with several major players holding strong positions across managed services, incident response, and technology solutions. Established providers such as CyberCX, Telstra Purple, Tesserent (a Thales company), Accenture Security, IBM Security, and Palo Alto Networks lead the market through their extensive service portfolios, national reach, and strong client relationships across critical sectors. However, the entry of specialised niche firms and the growing role of cloud-native security platforms from vendors like CrowdStrike, Fortinet, and Check Point have diversified the competitive landscape, offering organisations more tailored solutions, advanced threat intelligence, and sector-specific cybersecurity capabilities.
Name | Founding Year | Headquarters |
CyberCX | 2019 | Melbourne, Australia |
Telstra Purple | 2018 (brand launch) | Sydney, Australia |
Tesserent (a Thales company) | 1988 | Melbourne, Australia |
Sekuro | 2021 | Sydney, Australia |
NTT Security | 1988 (NTT Group) | Tokyo, Japan |
Optus Business | 1992 | Sydney, Australia |
Macquarie Cloud Services | 2001 | Sydney, Australia |
Accenture Security | 1989 (Accenture) | Dublin, Ireland |
Deloitte Cyber | 1845 (Deloitte) | London, UK |
KPMG Cyber | 1987 (KPMG Australia) | Sydney, Australia |
Some of the Recent Competitor Trends and Key Information About Competitors Include:
CyberCX: As one of Australia’s largest dedicated cybersecurity service providers, CyberCX has expanded its managed detection and response (MDR) offerings in 2024, opening new onshore Security Operations Centres (SOCs) in Melbourne and Perth. The company has also partnered with the Australian Cyber Security Centre (ACSC) to deliver Essential Eight maturity uplift programs for critical infrastructure operators.
Telstra Purple: Leveraging its nationwide telecommunications footprint, Telstra Purple has integrated advanced threat intelligence capabilities into its managed services portfolio in 2024. The business has focused on developing sovereign cloud security solutions for government and defense clients, ensuring data residency and compliance with SOCI Act requirements.
Tesserent (a Thales company): Following its acquisition by Thales, Tesserent has introduced enhanced incident response retainers and OT/ICS security services in 2024. The company has deepened its presence in the energy and utilities sector, securing contracts to protect operational technology in electricity distribution networks spanning over 700,000 km.
Palo Alto Networks: A global cybersecurity leader with strong local operations, Palo Alto Networks launched new Zero Trust Network Access (ZTNA) solutions tailored for Australian enterprises in 2024. The company has also invested in regional cloud infrastructure to improve performance and meet IRAP compliance for federal clients.
CrowdStrike: Known for its endpoint detection and response (EDR) technology, CrowdStrike recorded significant adoption growth among Australian SMEs in 2024. The firm has partnered with multiple MSSPs to integrate Falcon platform telemetry into broader XDR frameworks, reducing mean time to detection (MTTD) for customers across finance, healthcare, and retail sectors.
What Lies Ahead for Australia Cybersecurity Market?
The Australia Cybersecurity Market is expected to maintain strong momentum through 2030, supported by increasing regulatory requirements, heightened cyber threat activity, and continued digital infrastructure expansion. With over 12.44 million premises ready to connect to the NBN, 34 million mobile services in operation, and 11 regulated critical infrastructure sectors under the SOCI framework, the cybersecurity ecosystem will remain central to Australia’s economic resilience. The convergence of sovereign cloud demand, OT security needs, and AI-driven threat detection will be core growth catalysts for the years ahead.
Rise of Integrated Security Platforms: The future of Australia’s cybersecurity landscape will be shaped by increased adoption of integrated platforms that combine endpoint, network, cloud, and identity protections into unified frameworks. This is driven by the complexity of managing 2.66 million businesses’ diverse technology stacks and the operational efficiency benefits of reducing fragmented tooling.
Stronger OT/ICS Security Uplift: As energy networks spanning 767,798 km in distribution and 43,885 km in transmission integrate renewable generation and smart assets, OT/ICS cybersecurity will become a high-priority investment area. Real-time monitoring, anomaly detection, and segmentation strategies will be scaled to protect safety-critical systems from sophisticated cyber-physical attacks.
Expansion of Sector-Specific Security Programs: Industries such as finance, healthcare, government, and energy will see accelerated investment in tailored cybersecurity solutions. For example, the healthcare sector’s growing digital patient records and telehealth infrastructure will demand more privacy-focused controls, while the finance sector will deepen its fraud detection, transaction monitoring, and compliance automation capabilities.
Leveraging AI, Automation, and Threat Intelligence Fusion: AI and automation will be increasingly embedded into SOC operations to handle alert triage, predictive threat modelling, and automated containment. With ACSC handling 36,700 hotline calls and over 1,100 incidents in a year, advanced analytics and machine learning will help shorten response times, improve detection fidelity, and enable proactive defence through real-time threat intelligence fusion.
Australia Cybersecurity Market Segmentation
By Offering
Solutions
Network Security
Endpoint Security / XDR
Cloud Security (CSPM, CWPP, CASB)
Application & API Security
Data Security / DLP / DSPM
Identity & Access Management (IAM, PAM, MFA)
Email Security
OT / ICS Security
Threat Intelligence Platforms
Governance, Risk & Compliance (GRC) Tools
Services
Managed Security Services (MSSP, MDR, MXDR)
Professional Services & Advisory
Incident Response & Digital Forensics (DFIR)
Compliance & Audit Readiness
Security Awareness & Training
Penetration Testing / Red Team Engagements
SOC Build-Operate-Transfer Services
By Deployment Mode
On-Premises
Cloud-Based
Hybrid
Sovereign Cloud
Edge / OT Environments
By Organization Size
Micro & Small Enterprises
Lower Mid-Market
Upper Mid-Market
Large Enterprises
Government & Public Sector
By Industry Vertical
Financial Services & Banking
Healthcare & Life Sciences
Government & Defense
Energy & Utilities
Communications & Media
Mining & Resources
Retail & E-commerce
Education & Research
Transportation & Logistics
Manufacturing & Industrial
By Compliance Driver / Buyer Intent
Privacy & Data Breach Response (OAIC, Privacy Act)
APRA CPS 234 Compliance
SOCI Act Risk Management Program
Essential Eight Uplift Programs
IRAP / ISM Obligations
Cyber Insurance Requirements
International Standards Alignment (ISO 27001, SOC 2)
By Region
New South Wales
Victoria
Queensland
Western Australia
South Australia
Australian Capital Territory
Tasmania
Northern Territory
Players Mentioned in the Report:
CyberCX
Telstra Purple
Tesserent
Accenture Security
IBM Security
Cisco Systems
Fortinet
Check Point Software Technologies
Palo Alto Networks
CrowdStrike
McAfee
CyberArk
Imperva Australia
DXC Technology
FireEye
Key Target Audience
Chief Information Security Officers (Enterprises & Government agencies)
Chief Risk Officers (Financial Services / Critical Infrastructure)
Cyber Insurance Underwriters / Risk Assessment Teams
Investment & Venture Capital Firms (cybersecurity funds)
Sovereign Wealth / Infrastructure Investment Bodies
Government Agencies: Australian Signals Directorate (ASD), Australian Cyber Security Centre (ACSC)
Digital Transformation Leads (Large Enterprises)
IT Security Procurement Heads (Federal & State Governments)
Time Period:
Historical Period: 2019-2024
Base Year: 2025
- Forecast Period: 2025-2030
Report Coverage
Choose individual sections to purchase. Mix and match as you like.
4.1. Delivery Model Analysis for Cybersecurity-Managed Services, On-Premises Solutions, Cloud Security Platforms, Hybrid Deployments-Discussion on Margins, Client Preferences, Strengths and Weaknesses
4.2. Revenue Streams for Australia Cybersecurity Market
4.3. Business Model Canvas for Australia Cybersecurity Market
5.1. MSSPs vs. In-House Security Operations (SOC)
5.2. Investment Model in Australia Cybersecurity Market
5.3. Comparative Analysis of Incident Response Funnel Process by Private and Government Organisations in Australia Cybersecurity Market
5.4. Cybersecurity Budget Allocation by Organisation Size, 2025
8.1. Revenues, 2019-2025
9.1. By Offering (Solutions, Services), 2024-2025P
9.2. By Security Type (Network Security, Endpoint Security, Cloud Security, Application Security, Data Security, Identity & Access Management, OT/ICS Security), 2024-2025P
9.3. By Industry Vertical (Financial Services, Healthcare, Government & Defense, Energy & Utilities, Retail & E-commerce, Education, Manufacturing), 2024-2025P
9.3.1. By Type of Financial Services Security Solutions, 2024-2025P
9.3.2. By Type of Healthcare Security Solutions, 2024-2025P
9.3.3. By Type of Energy & Utilities Security Solutions, 2024-2025P
9.3.4. By Type of Retail & E-commerce Security Solutions, 2024-2025P
9.4. By Organisation Size (Large Enterprises, Medium-Sized Enterprises, SMEs, Government), 2024-2025P
9.5. By Compliance Driver (Privacy & Data Breach, SOCI, APRA CPS 234, Essential Eight, IRAP, Cyber Insurance Requirements), 2024-2025P
9.6. By Deployment Mode (On-Premises, Cloud-Based, Hybrid, Sovereign Cloud, Edge/OT), 2024-2025P
9.7. By Threat Vector (Ransomware, Phishing/Social Engineering, Supply Chain Attacks, Insider Threats, Zero-Day Exploits), 2024-2025P
9.8. By Region (New South Wales, Victoria, Queensland, Western Australia, South Australia, Tasmania, Northern Territory, Australian Capital Territory), 2024-2025P
10.1. Enterprise Client Landscape and Cohort Analysis
10.2. Cybersecurity Needs and Decision-Making Process
10.3. Security Program Effectiveness and ROI Analysis
10.4. Gap Analysis Framework
11.1. Trends and Developments for Australia Cybersecurity Market
11.2. Growth Drivers for Australia Cybersecurity Market
11.3. SWOT Analysis for Australia Cybersecurity Market
11.4. Issues and Challenges for Australia Cybersecurity Market
11.5. Government Regulations for Australia Cybersecurity Market
12.1. Market Size and Future Potential for Cloud Security Industry in Australia, 2019-2030
12.2. Business Model and Revenue Streams
12.3. Deployment Models and Security Offerings
12.4. Cross Comparison of Leading Cloud Security Companies based on Company Overview, Certifications (IRAP, ISO 27001), Revenues, Number of Clients, Revenue Streams, Number of Security Modules, Pricing Models, and other Variables
15.1. Market Share of Key Players in Australia Cybersecurity Market by Revenues, 2023
15.2. Benchmark of Key Competitors in Australia Cybersecurity Market Including Variables such as Company Overview, USP, Business Strategies, Business Model, SOC Locations, Revenues, Pricing Basis Service Type, Technology Stack, Best-Selling Solutions, Major Clients, Strategic Tie-Ups, Marketing Strategy, and Recent Developments
15.3. Operating Model Analysis Framework
15.4. Gartner Magic Quadrant Positioning (Security Technology & MSSPs)
15.5. Bowmans Strategic Clock for Competitive Advantage
16.1. Revenues, 2025-2030
17.1. By Offering (Solutions, Services), 2025-2030
17.2. By Security Type (Network, Endpoint, Cloud, Application, Data, IAM, OT/ICS), 2025-2030
17.3. By Industry Vertical (Financial Services, Healthcare, Government & Defense, Energy & Utilities, Retail & E-commerce, Education, Manufacturing), 2025-2030
17.3.1. By Type of Financial Services Security Solutions, 2025-2030
17.3.2. By Type of Healthcare Security Solutions, 2025-2030
17.3.3. By Type of Energy & Utilities Security Solutions, 2025-2030
17.3.4. By Type of Retail & E-commerce Security Solutions, 2025-2030
17.4. By Organisation Size (Large Enterprises, Medium-Sized Enterprises, SMEs, Government), 2025-2030
17.5. By Compliance Driver (Privacy & Data Breach, SOCI, APRA CPS 234, Essential Eight, IRAP, Cyber Insurance Requirements), 2025-2030
17.6. By Deployment Mode (On-Premises, Cloud-Based, Hybrid, Sovereign Cloud, Edge/OT), 2025-2030
17.7. By Threat Vector (Ransomware, Phishing/Social Engineering, Supply Chain Attacks, Insider Threats, Zero-Day Exploits), 2025-2030
17.8. By Region (New South Wales, Victoria, Queensland, Western Australia, South Australia, Tasmania, Northern Territory, Australian Capital Territory), 2025-2030
Research Methodology
Step 1: Ecosystem Creation
We begin by mapping the complete ecosystem of the Australia Cybersecurity Market, identifying both demand-side and supply-side entities. On the demand side, this includes critical infrastructure operators, federal and state government agencies, financial institutions, healthcare providers, retail and e-commerce companies, energy and utilities operators, and SMEs adopting digital transformation. On the supply side, we consider managed security service providers (MSSPs), consulting integrators, global cybersecurity vendors, niche local security firms, cloud service providers, and incident response specialists. Based on this ecosystem mapping, we shortlist 5–6 leading cybersecurity providers in the country by evaluating their financial performance, market reach across sectors and regions, service breadth, government certifications (such as IRAP), and client base. Sourcing for this mapping involves a review of government and industry reports, public domain announcements, press releases, and trusted secondary and proprietary databases to consolidate a complete view of the industry.
Step 2: Desk Research
We then conduct an exhaustive desk research exercise using diverse secondary and proprietary databases to compile a detailed analysis of the Australian cybersecurity landscape. This includes data aggregation on the number of active providers, their service portfolios, deployment models, technology capabilities, vertical penetration, and cross-sector engagement. We analyse industry-level metrics such as workforce capacity in cybersecurity roles, incidence of regulatory reporting (e.g., Notifiable Data Breaches), volume of ACSC advisories, and infrastructure expansion indicators like NBN premises ready to connect. Company-level analysis involves reviewing annual reports, investor presentations, ASX filings, government procurement records, press releases, and compliance attestations. We use this information to assess market positioning, incident response capacity, SOC locations, sovereign cloud capabilities, pricing structures, and recurring revenue streams.
Step 3: Primary Research
We engage in in-depth interviews with C-suite executives (CISOs, CTOs, CIOs, and Managing Directors), government cybersecurity officials, and senior decision-makers from target sectors. These interviews serve to validate desk research findings, test market hypotheses, authenticate operational and performance metrics, and gather insights into challenges such as skills shortages, compliance complexity, and tool fragmentation. Our approach includes a bottom-up revenue contribution assessment for each shortlisted player to aggregate a reliable market view. As part of our validation strategy, we also conduct disguised client-style inquiries with selected MSSPs and solution vendors. This enables verification of service capabilities, SOC staffing levels, SLAs, pricing tiers, and contract structures. We corroborate responses against procurement data, security certification registers, and regulatory compliance disclosures to ensure data integrity.
Step 4: Sanity Check
Finally, we perform a dual sanity check through both bottom-up and top-down modelling. Bottom-up aggregation is based on validated revenue contributions from primary and secondary research for each major player, while top-down analysis uses macroeconomic indicators (such as ICT investment levels, sectoral digital adoption rates, and incident volume data from ACSC) to benchmark our market model. Any discrepancies are reconciled through iterative data validation and expert follow-ups. This ensures the final Australia Cybersecurity Market size and segmentation outputs are consistent, reliable, and fully defensible for strategic decision-making.
FAQs
01 What is the potential for the Australia Cybersecurity Market?
The Australia Cybersecurity Market is positioned for robust expansion, with demand accelerating due to heightened cyber threat activity, regulatory compliance mandates, and the rapid adoption of cloud and digital services. Growth is underpinned by the presence of 2.66 million actively trading businesses, widespread broadband penetration with over 12.44 million premises ready to connect, and critical infrastructure digitisation across 11 regulated sectors. The market’s potential is reinforced by increased investment from both the public and private sectors in identity-first security, sovereign cloud solutions, and managed detection and response services.
02 Who are the Key Players in the Australia Cybersecurity Market?
The Australia Cybersecurity Market features several leading players, including CyberCX, Telstra Purple, and Tesserent (a Thales company). These organisations dominate due to their extensive service portfolios, strong client relationships across critical industries, and onshore SOC capabilities. Other notable participants include Accenture Security (Australia), IBM Security, Cisco Systems, Fortinet, Check Point, Palo Alto Networks, and CrowdStrike. Collectively, these players drive innovation, deliver incident response at scale, and support both government and private enterprises in meeting stringent compliance and resilience objectives.
03 What are the Growth Drivers for the Australia Cybersecurity Market?
Key growth drivers include Australia’s GDP of USD 1.77 trillion and a digitally connected population of over 27.2 million, creating an expansive attack surface. The 34 million mobile services in operation and quarterly broadband data volumes exceeding 13.9 million terabytes reflect deep digital adoption, increasing the need for robust security frameworks. Regulatory initiatives such as the Security of Critical Infrastructure Act, OAIC Notifiable Data Breaches scheme, and APRA CPS 234 are further spurring investment in advanced threat protection, compliance automation, and managed security services across industries.
04 What are the Challenges in the Australia Cybersecurity Market?
The market faces notable challenges, including a persistent cybersecurity skills shortage, with 339,400 national job vacancies and limited specialist availability. Legacy technology across 767,798 km of electricity distribution networks and 43,885 km of transmission lines complicates OT security modernisation. Tool fragmentation is another issue, as 2.66 million businesses operate diverse device fleets, cloud environments, and identity systems, making unified policy enforcement difficult. Additionally, compliance burdens from 11 regulated critical sectors and 1,113 notifiable data breaches in a year require significant resource allocation for governance and audit readiness.