India Cybersecurity Market Outlook To 2030
By Solution Type, By Security Domain, By Deployment Model, By Security Architecture, By Organization Size, By End-User Industry, and By Region
- Product Code: TDR0313
- Region: Asia
- Published on: September 2025
- Total Pages: 80
Report Summary
The report titled “India Cybersecurity Market Outlook to 2030 – By Solution Type, By Security Domain, By Deployment Model, By Security Architecture, By Organization Size, By End-User Industry, and By Region” provides a comprehensive analysis of India’s cybersecurity industry. The report covers an overview and genesis of the industry, overall market size in terms of revenue, detailed market segmentation; trends and developments, regulatory landscape, customer-level profiling, issues and challenges, and competitive landscape including competition scenario, cross-comparison, opportunities and bottlenecks, and company profiling of major players in the cybersecurity market. The report concludes with future market projections based on security spend drivers, incident volumes, compliance adoption, cloud workload intensity, regions, cause-and-effect relationships, and success case studies highlighting the major opportunities and cautions.
India Cybersecurity Market Overview and Size
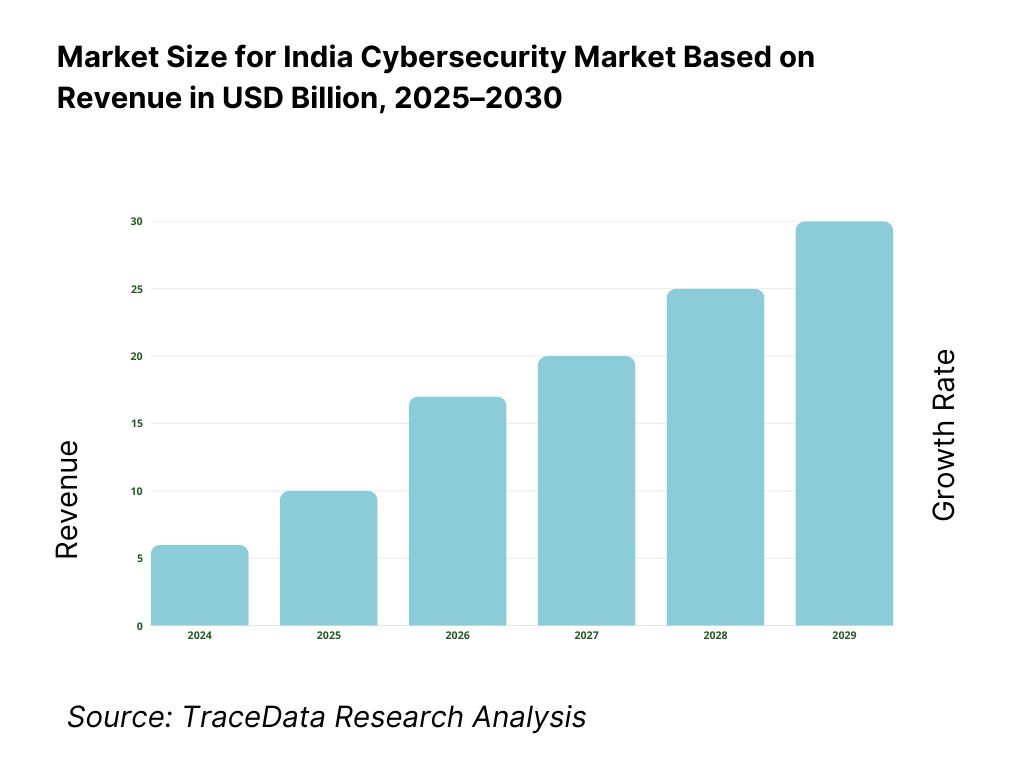
The India cybersecurity market is valued at USD 5.8 billion, grounded in a comprehensive multi-source historical analysis. This valuation reflects substantial growth across product, services, and managed security segments. It is driven by rapid digitization, expanding cloud infrastructure, stringent data protection mandates, and elevated cybersecurity budgets across enterprises and public-sector entities, all backed by reliable industry and advisory reports.
Major urban hubs such as Bengaluru, Mumbai, Hyderabad, and Delhi–NCR lead the cybersecurity landscape. These cities dominate due to dense concentrations of enterprise IT hubs, thriving startup ecosystems, and regional headquarters of key global cloud and security vendors. Additionally, government-led digital infrastructure projects in these areas bolster local demand and strengthen specialized cybersecurity capabilities.
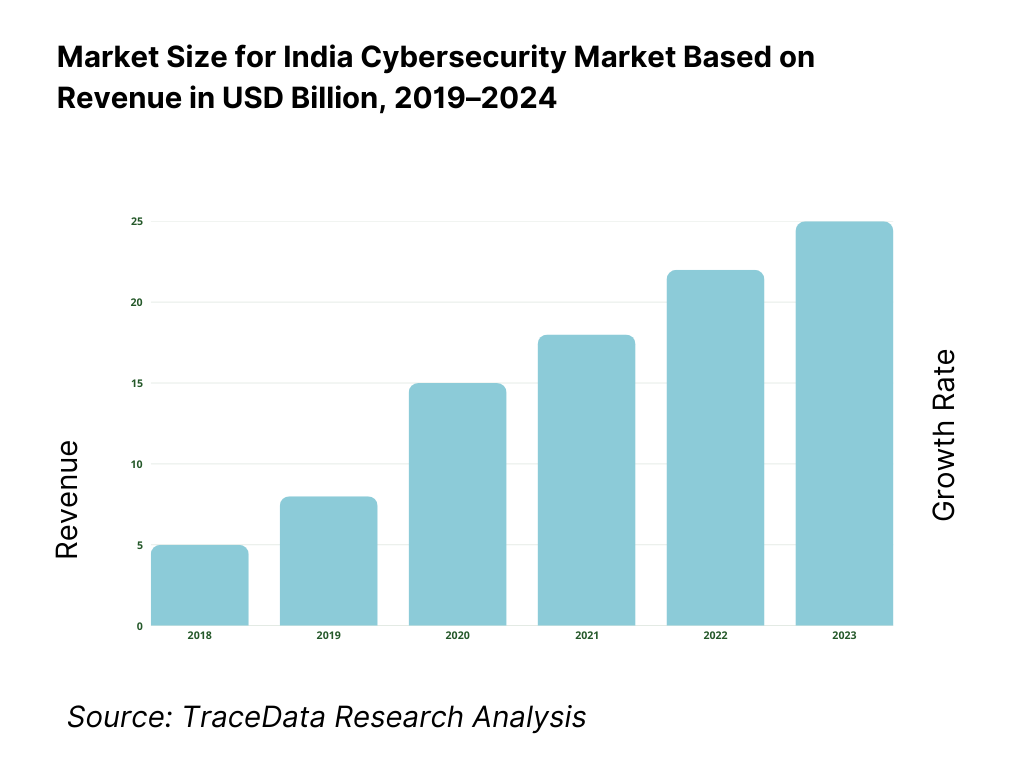
What Factors are Leading to the Growth of the India Cybersecurity Market:
Scale and velocity of digital transactions (UPI, Aadhaar, DigiLocker) are expanding the attack surface and compliance needs. Monthly retail rails are operating at unprecedented loads: UPI processed 16.58 billion transactions in one recent month with value of ₹23.48 lakh crore, and ended the year with 16.73 billion transactions in the final month. Identity and document rails are equally pervasive: cumulative Aadhaar authentications have crossed 15,223 crore and DigiLocker shows 55+ crore registered users with 943.90+ crore issued documents. This transaction and identity density materially elevates enterprise exposure, drives stringent logging/monitoring, and sustains demand for managed detection, fraud analytics, and identity security across Indian corporates.
Ubiquitous connectivity—mobile-first broadband and nationwide 5G—pushes cybersecurity into every business workflow. Regulators count 924.07 million broadband subscriptions, including 884.01 million wireless and 40.06 million wired lines. The digital backbone is spreading quickly: India reports 96.96 crore internet connections, 4.74 lakh 5G sites, with coverage reaching 99.6% of districts. This mobile-first fabric means enterprises must secure remote endpoints, mobile apps, APIs, and edge nodes at scale, adopt zero-trust access, and harden cloud/SaaS usage against credential stuffing and session hijacks that ride on ever-available networks.
Official incident and crime tallies show rising hostile activity, forcing deeper investment in protection and response. National cyber incident reporting recorded 13,91,457 cases, then 15,92,917, and then 20,41,360 across successive years, while law-enforcement documented 65,893 cybercrime cases in the latest compiled year. CERT-In has also conducted 109 national drills engaging 1,438 organizations and has 200 empanelled security auditing organisations to bolster resilience. These official numbers catalyze enterprise budgets for SIEM/SOAR, endpoint containment, phishing defense, incident retainers, and tabletop exercises anchored in regulator-mandated reporting windows.
Which Industry Challenges Have Impacted the Growth of the India Cybersecurity Market:
MSME digitalization outpaces security capacity, widening enterprise risk at the edge. Formalization has created a vast digitally connected long-tail: 4.76 crore MSMEs are registered across the Udyam and Assist platforms, rising to 5.70 crore by late year, yet fixed broadband lines remain 40.06 million against 884.01 million wireless, making security heavily mobile-centric. With 96.96 crore internet connections and 4.74 lakh 5G sites, endpoints sprawl across geographies. Many MSMEs lack dedicated CISOs or SOC coverage, delaying patching and MFA rollouts; this leaves suppliers in large enterprise value chains as soft targets, complicating third-party risk assurance for corporates.
Cybercrime pressure on enterprises and citizens strains response, investigation, and recovery. NCRB registered 65,893 cybercrime cases in the latest compiled year, while CERT-In tracked 20,41,360 cybersecurity incidents in the following year. At the same time, monthly digital payments like UPI touched 16.58 billion transactions, raising the exposure to phishing, mule accounts and merchant frauds; Aadhaar authentications surpass 15,223 crore, expanding identity attack vectors. This volume burdens enterprise fraud ops, DFIR capacity, and law-enforcement coordination, increasing the need for transaction risk scoring, real-time identity proofing, takedown services, and breach notification workflows aligned to statutory timelines.
Audit/compliance bandwidth is tight relative to ecosystem size, creating execution risk. CERT-In lists 200 empanelled security auditing organisations to support compliance under national directions, but the formal enterprise base already exceeds 4.76–5.70 crore MSMEs with millions more connections (96.96 crore) and heavy-duty rails (UPI 16.73 billion monthly peak). Meanwhile, sector regulators (e.g., securities and insurance) impose specific reporting clocks and periodic audits. The imbalance between regulated workloads and available certified audit capacity raises costs of delays, heightens the risk of non-compliance, and necessitates automation (log retention, vulnerability remediation tracking) plus year-round assessment cycles.
What are the Regulations and Initiatives which have Governed the Market:
CERT-In Directions under the IT Act require fast incident reporting, synchronized clocks, and long-horizon log retention. Government memoranda implementing the Directions mandate reporting cyber incidents to CERT-In within 6 hours, retention of all ICT logs for 180 days, and NTP time-sync to trace incidents. CERT-In confirms nationwide enforcement of these directions and provides sectoral support via CSIRT-Fin, cyber drills (109 conducted, 1,438 entities engaged) and an empanelled list of 200 auditing organisations. Enterprises operating in India must embed 6-hour notification playbooks, 180-day log architectures, and regulator-ready evidence trails into their SOC runbooks.
SEBI’s Cybersecurity & Cyber Resilience Framework (CSCRF) fixes tight clocks and recurring audit deliverables for market entities. Circulars require stockbrokers/depository participants to notify SEBI/Exchanges/CERT-In within 6 hours of detection; submit quarterly cyber incident reports within 15 days from quarter-end; and furnish root-cause analysis within 30 days after an event, alongside audits at specified periodicity under the CSCRF consolidation. These numeric obligations materially shape control environments for BFSI intermediaries—tightening EDR/SIEM integration, breach communication trees, and Board-level cyber oversight.
Digital Personal Data Protection Act codifies penalties up to ₹250 crore per contravention, raising the cost of lax safeguards. The enacted law empowers the Data Protection Board to levy monetary penalties capped at ₹250 crore per breach category; authoritative summaries specify ₹250 crore for failure to implement reasonable security safeguards, and additional slabs (e.g., ₹200 crore for children’s-data obligations). This elevates board-level accountability for breach prevention, breach notification to the Board/affected individuals, and DPIA/audit programs—directly stimulating investments in encryption, key management, DLP, and vendor-risk controls across India-resident and cross-border processing.
India Cybersecurity Market Segmentation
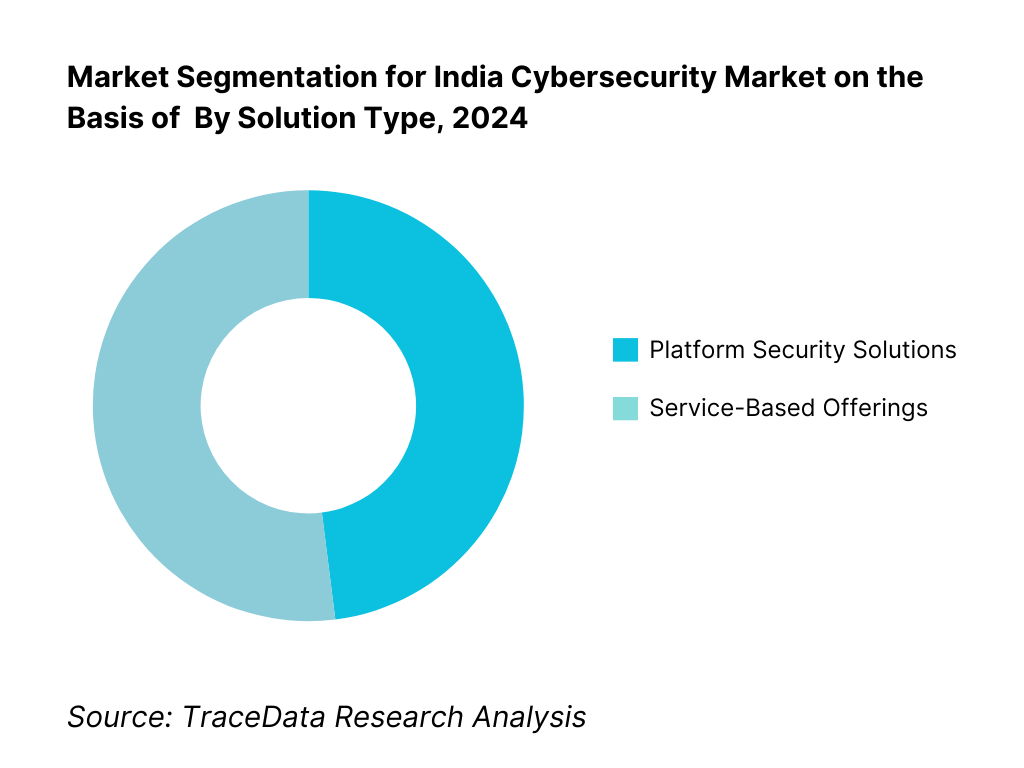
By Solution Type: The service-based MDR segment holds the dominant market share in 2024. Its prominence is underpinned by enterprise preference for outsourced, round-the-clock threat detection paired with remediation capabilities. Many firms, constrained by scarce in-house security talent and complexity of evolving threats, favor MDR for its proactive threat hunting, immediate operational support, and compliance adherence—making it a cost-effective and strategic choice.
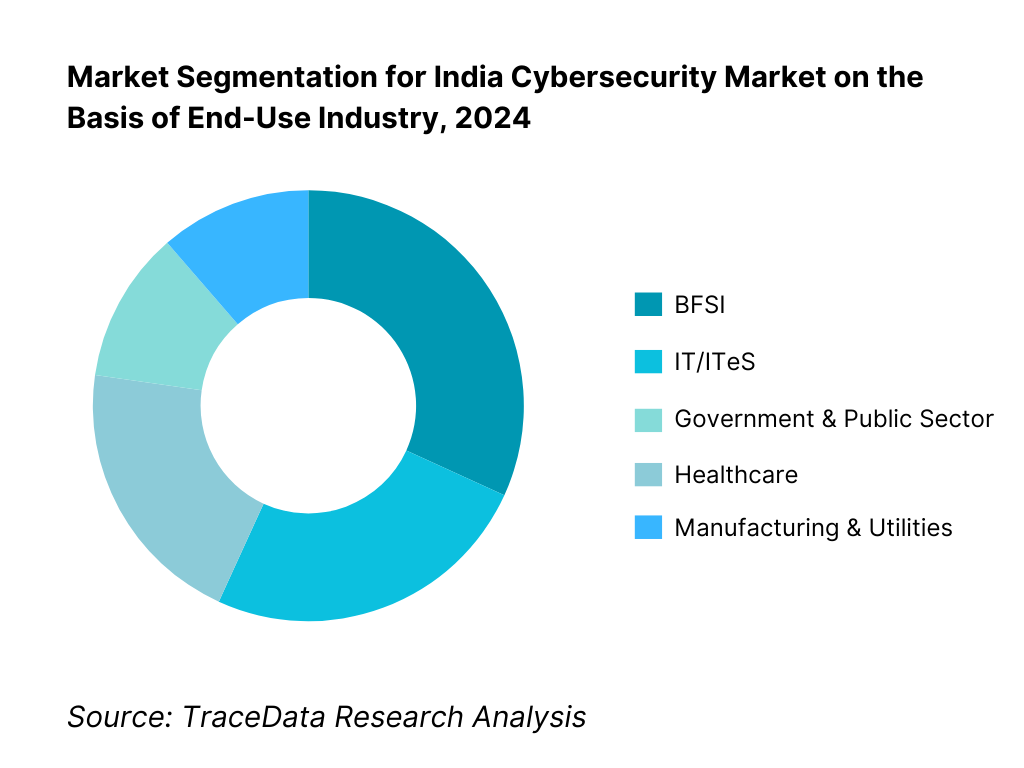
By End-User Industry: BFSI leads share in 2024. This dominance stems from highly regulated frameworks, exposure to digital fraud, large-scale customer data volumes, and mandatory compliance demands. Financial institutions are rigorous about adopting multi-layered cybersecurity solutions, putting BFSI at the forefront of investment among verticals.
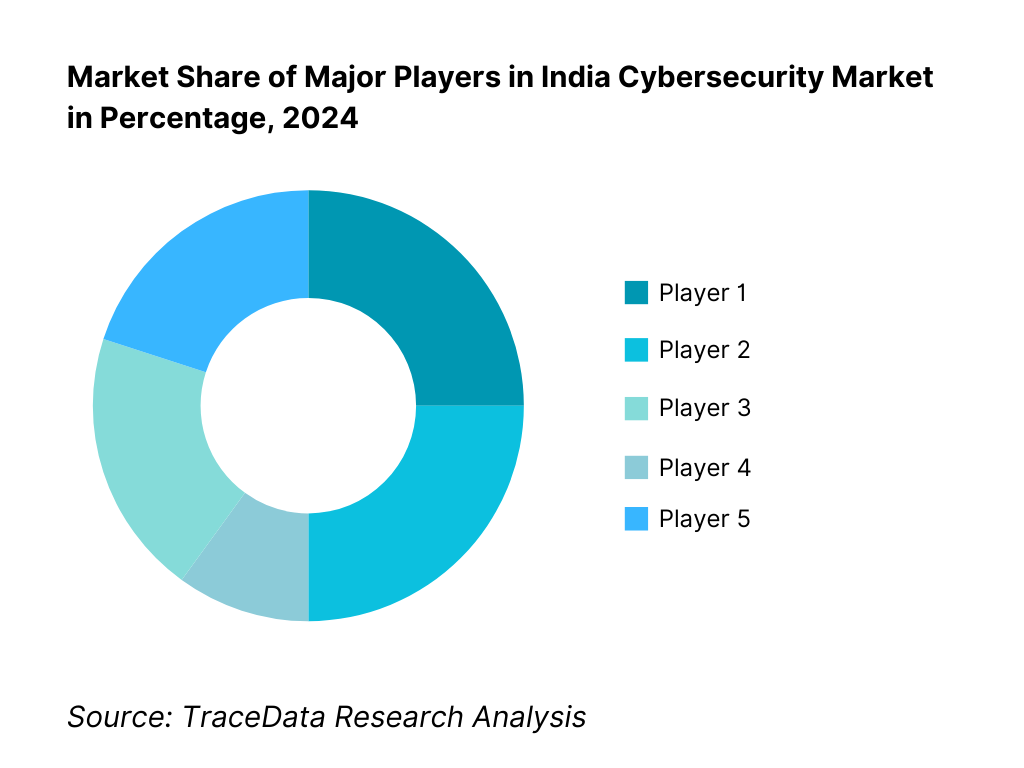
Competitive Landscape in India Cybersecurity Market
The India cybersecurity market features a mix of global giants, domestic champions, MSSPs, and cloud-centric platforms. Top-tier players include international tech leaders and specialized Indian vendors offering tailored solutions—highlighting a competitive yet collaborative ecosystem.
Name | Founding Year | Original Headquarters |
Palo Alto Networks | 2005 | Santa Clara, USA |
Cisco Security | 1984 | San Jose, USA |
Fortinet | 2000 | Sunnyvale, USA |
Check Point | 1993 | Tel Aviv, Israel |
CrowdStrike | 2011 | Sunnyvale, USA |
Zscaler | 2007 | San Jose, USA |
Trend Micro | 1988 | Tokyo, Japan |
Sophos | 1985 | Abingdon, UK |
Trellix (McAfee + FireEye) | 2022 (merger) | Milpitas, USA |
IBM Security | 1911 | Armonk, USA |
Rapid7 | 2000 | Boston, USA |
Tenable | 2002 | Columbia, USA |
Quick Heal (Seqrite) | 1993 | Pune, India |
Safe Security | 2015 | Palo Alto, USA & Bangalore, India |
Microsoft Security | 1975 | Redmond, USA |
Some of the Recent Competitor Trends and Key Information About Competitors Include:
Palo Alto Networks: A leading global cybersecurity provider, Palo Alto Networks has significantly strengthened its presence in India with expanded SOC operations in Bangalore and Mumbai. In 2024, the company introduced advanced Zero Trust and SASE frameworks for BFSI and government clients, aligning with India’s regulatory push on data protection and critical infrastructure security.
Cisco Security: Cisco has enhanced its SecureX platform in India by integrating endpoint, network, and cloud protection into a unified architecture. The company also launched partnerships with Indian system integrators in 2024, helping enterprises adopt cloud-native cybersecurity solutions with stronger compliance features for RBI and SEBI-regulated institutions.
Fortinet: Known for its security-driven networking and ASIC-powered firewalls, Fortinet reported double-digit growth in India in 2024. The company expanded its SD-WAN and OT/ICS security offerings, targeting manufacturing and utility sectors that are increasingly exposed to cyber threats in India.
Check Point: Check Point has launched its Infinity architecture for Indian enterprises, focusing on cloud posture management and advanced threat prevention. In 2024, the company increased its partnerships with managed security service providers (MSSPs), aiming to expand its reach among mid-market enterprises in India.
CrowdStrike: With its Falcon platform gaining traction in India, CrowdStrike recorded rapid growth in endpoint detection and response (EDR) adoption during 2024. The company is investing in local partnerships and cloud delivery to support SMEs and startups facing growing ransomware threats.
What Lies Ahead for India Cybersecurity Market?
The India cybersecurity market is expected to expand robustly by 2030, supported by the intensifying pace of digital adoption, increasing regulatory enforcement around data protection, and rising sophistication of cyberattacks across industries. Growth will be further accelerated by the widespread migration to cloud-native platforms, the expansion of 5G networks, and government-backed initiatives promoting secure digital infrastructure. Enterprises of all sizes will be compelled to make cybersecurity a boardroom priority, driving long-term investment in defensive and offensive security capabilities.
Zero-Trust and SASE Expansion: The future of cybersecurity in India will be shaped by the accelerated adoption of Zero-Trust frameworks and Secure Access Service Edge (SASE) solutions. With workforces distributed across geographies and cloud workloads multiplying, these architectures will provide unified, identity-based security while ensuring compliance with CERT-In and DPDP obligations.
AI and Automation in Threat Defense: The growing scale of cyber incidents will push enterprises to adopt AI-driven threat detection, automated response playbooks, and predictive analytics. These technologies will reduce mean time to detect (MTTD) and mean time to respond (MTTR), helping organizations cope with high-volume threats such as ransomware, phishing, and insider risks more efficiently.
Rise of Managed Security Services (MSS): With a chronic shortage of skilled security professionals, India will witness the rapid scaling of Managed Detection and Response (MDR) and SOC-as-a-Service offerings. MSSPs and telcos will increasingly bundle compliance reporting, incident handling, and continuous monitoring—especially for SMEs and PSUs that cannot maintain large in-house teams.
Sector-Specific Cybersecurity Demands: Industries such as BFSI, healthcare, manufacturing, and telecom will require highly tailored security frameworks. BFSI will focus on fraud prevention and data leakage protection, healthcare will prioritize safeguarding patient records and medical IoT, and manufacturing will emphasize OT/ICS resilience. This sectoral customization will create opportunities for niche solution providers.
India Cybersecurity Market Segmentations
By Solution Type
Network Security
Endpoint Security
Cloud Security
Application & API Security
Identity & Access Management (IAM/PAM)
Data Loss Prevention (DLP)
OT/IoT Security
By Deployment Mode
On-Premises
Cloud-Based (SaaS / Security-as-a-Service)
Hybrid
By Security Service
Managed Security Services (MSS/MDR)
Professional Services (Consulting, VAPT, Compliance Audits)
Incident Response & Remediation
SOC-as-a-Service
By Industry Vertical
BFSI
Government & Defense
IT/ITeS & Telecom
Healthcare
Manufacturing & Energy
Retail & E-Commerce
By Organization Size
Large Enterprises
Medium-Sized Enterprises
Small Enterprises / SMEs
Public Sector Undertakings (PSUs)
Players Mentioned in the Report:
Palo Alto Networks
Cisco Security
Quick Heal (Seqrite)
Safe Security
Trend Micro
CrowdStrike
Zscaler
Fortinet
Check Point
Microsoft Security
IBM Security
Sophos
Trellix
Tenable
Rapid7
Key Target Audience
Chief Information Security Officers (CISOs) and Heads of Cybersecurity
Chief Information Officers (CIOs)
Enterprise Procurement and Budget Heads
Enterprise Risk & Compliance Officers
IT Security Heads in BFSI, Government & Defense
Investments and Venture Capitalist Firms (cybersecurity funds)
Government and Regulatory Bodies (MeitY, CERT-In, RBI, SEBI, IRDAI, NCIIPC)
Cybersecurity Practice Leaders in large enterprise chains
Time Period:
Historical Period: 2019-2024
Base Year: 2025
Forecast Period: 2025-2030
Report Coverage
Choose individual sections to purchase. Mix and match as you like.
4.1. Delivery Model Analysis for Cybersecurity [On-Premises, Cloud-Native, Hybrid, Managed Services]-Margins, Preference, Strengths & Weaknesses
4.2. Revenue Streams for Cybersecurity Market [Product Licenses, Subscription Models, SaaS Security, MDR/XDR Services, Compliance Consulting, Incident Response Retainers]
4.3. Business Model Canvas for Cybersecurity [Vendor, MSSP, Telco-Led Security, Startup Ecosystem]
5.1. Point Security Tools vs. Integrated Security Platforms [SIEM/XDR/SASE]
5.2. Investment Models in Cybersecurity [Enterprise In-House SOC vs Outsourced MSSP]
5.3. Comparative Analysis of Cyber Defense Approaches by Private vs Government Organizations [Incident Response SOPs, Procurement Models, Skill Investments]
5.4. Cybersecurity Budget Allocation by Company Size [Large Enterprises, Mid-Market, SMEs, PSUs]
8.1. Revenues [Historical Market Evolution; CAGR by Segment]
9.1. By Market Structure [In-House Security Operations vs Outsourced MSSP]
9.2. By Security Domain [Network Security, Endpoint Security, Cloud Security, Application/API Security, Identity & Access Management, OT/ICS Security]
9.3. By Industry Verticals [BFSI, Government & Defense, IT/ITeS, Healthcare, Manufacturing, Telecom, Retail & E-Commerce, Energy & Utilities]
9.3.1. By Type of IT/ITeS Security [SOC-as-a-Service, Cloud Workload Protection, CNAPP]
9.3.2. By Type of BFSI Security [Fraud Management, Transaction Monitoring, Data Leakage Prevention]
9.3.3. By Type of Healthcare Security [Patient Data Protection, HIPAA/DPDP Compliance, Medical IoT Security]
9.3.4. By Type of Manufacturing/OT Security [ICS/SCADA Security, Zero-Trust OT, IIoT Defense]
9.4. By Company Size [Large Enterprises, Mid-Market, SMEs, PSUs]
9.5. By Employee Designation [CISOs, IT Security Managers, Security Analysts, Compliance Officers]
9.6. By Deployment Mode [On-Premises, Cloud-Native SaaS, Hybrid Security Models, Edge Security]
9.7. By Security Architecture [Zero-Trust, SASE/SSE, Micro-Segmentation, Threat Deception]
9.8. By Region [North India, West India, South India, East & North-East India; Metro vs Tier-2/3 Cities]
10.1. Corporate Client Landscape and Cohort Analysis [BFSI, Telecom, IT/ITeS, Startups, PSUs]
10.2. Cybersecurity Needs and Decision-Making Process [Procurement Drivers: Compliance, Breach Experience, Audit Requirements]
10.3. Cybersecurity Effectiveness & ROI Analysis [MTTD, MTTR, Attack Surface Reduction, Compliance Cost Avoidance]
10.4. Gap Analysis Framework [Coverage Gaps vs Emerging Threats]
11.1. Trends & Developments [SASE Adoption, XDR Convergence, AI/ML in Threat Hunting, Quantum-Readiness]
11.2. Growth Drivers [DPDP Compliance, 5G Rollouts, Cloud Migration, Digital Public Infrastructure Expansion]
11.3. SWOT Analysis [Strengths, Weaknesses, Opportunities, Threats of Indian Market]
11.4. Issues & Challenges [Talent Shortage, Legacy Infrastructure, Shadow IT, Vendor Fragmentation]
11.5. Government Regulations [CERT-In Directions, DPDP Act, RBI & SEBI Cyber Norms, NCIIPC for Critical Sectors]
12.1. Market Size & Future Potential for Cloud Security in India [SaaS, CNAPP, CSPM, CASB]
12.2. Business Models & Revenue Streams [Subscription, Usage-Based Pricing, Pay-As-You-Go]
12.3. Deployment Models & Security Offerings [Cloud-Native Firewalls, API Security, Identity-as-a-Service]
12.4. Cross-Comparison of Leading Cloud Security Companies [Company Overview, India Investments, Revenues, SOC Footprint, No. of Clients, Service Coverage, Pricing, Certifications]
15.1. Market Share of Key Players in India [by Security Domain; by MSSP; by Industry Vertical]
15.2. Benchmark of Key Competitors [Company Overview, USP, Strategy, Revenue Streams, Pricing, Modules, Clients, Tech Stack, India Presence, Recent Developments]
15.3. Operating Model Analysis Framework [Product-Led vs Service-Led Models]
15.4. Gartner Magic Quadrant for Security Domains [SIEM, Endpoint, Network, Cloud Security]
15.5. Bowman’s Strategic Clock for Competitive Advantage [Platformization vs Specialization]
16.1. Revenues [Forecast Market Evolution; CAGR by Segment]
17.1. By Market Structure [In-House vs MSSP, Forecast Period]
17.2. By Security Domain [Forecast: Network, Endpoint, Cloud, Application/API, OT/IoT]
17.3. By Industry Verticals [BFSI, IT/ITeS, Government, Healthcare, Manufacturing, Retail]
17.4. By Company Size [Large Enterprises, Mid-Market, SMEs, PSUs]
17.5. By Employee Designation [CISOs, Managers, Analysts, Compliance Roles]
17.6. By Deployment Mode [On-Prem, Cloud, Hybrid, Edge]
17.7. By Security Architecture [Zero-Trust, SASE/SSE, AI/ML Security]
17.8. By Region [North, South, East, West India; Tier-2/3 Growth]
Research Methodology
Step 1: Ecosystem Creation
We begin by mapping the India cybersecurity ecosystem, identifying all demand-side and supply-side entities. Demand-side entities include BFSI institutions, IT/ITeS firms, telecom operators, healthcare networks, manufacturing conglomerates, government agencies, and SMEs adopting digital platforms. Supply-side entities cover global cybersecurity vendors, domestic product developers, MSSPs, system integrators, cloud providers, and telco-led cybersecurity services. Based on this mapping, we shortlist 5–6 leading cybersecurity providers in the country by evaluating their financial disclosures, India revenue contribution, SOC footprint, partner network, and compliance credentials. Sourcing leverages government releases, CERT-In advisories, SEBI/RBI circulars, and secondary/proprietary databases to collate industry-level information.
Step 2: Desk Research
Next, we conduct exhaustive desk research across multiple secondary and proprietary databases. This analysis aggregates industry-level insights including the number of cybersecurity providers, service distribution (MSSP vs in-house), enterprise security spend allocation, and emerging domains like Zero Trust, SASE, and cloud-native security. We examine company-level data using annual reports, regulatory filings, press releases, SOC certifications, and financial statements of vendors. Sector-specific metrics such as BFSI audit compliance costs, telecom network security spending, and government digital infrastructure budgets are incorporated. The objective is to establish a foundational understanding of the India cybersecurity market, mapping both solution providers and enterprise adoption patterns.
Step 3: Primary Research
We then conduct in-depth interviews with CISOs, CIOs, SOC managers, MSSP executives, and regulators representing diverse enterprises and security vendors in India. These interviews validate statistical data, test hypotheses around growth drivers and challenges, and uncover operational insights such as SOC maturity levels, mean time to detect (MTTD), and mean time to respond (MTTR). A bottom-up approach is followed to estimate revenue contributions by individual vendors and services, which are then aggregated into the overall market. To strengthen accuracy, disguised interviews are undertaken with selected providers under the guise of potential clients, helping us verify claims around deployment volumes, pricing models, response SLAs, and value-chain processes. This triangulation enhances reliability of the data.
Step 4: Sanity Check
Finally, a top-down and bottom-up reconciliation is conducted to ensure accuracy of the findings. Top-down models derive estimates from macro indicators such as ICT spend, BFSI IT allocations, and government digital infrastructure budgets. Bottom-up analysis aggregates revenue from vendors, MSSPs, and solution sub-segments. These approaches are cross-validated against regulatory compliance requirements (CERT-In, DPDP Act, RBI/SEBI frameworks) and adoption benchmarks to confirm robustness. This dual-layer modeling exercise ensures the market size and forecasts are logically consistent, statistically reliable, and aligned with India’s rapidly evolving cybersecurity ecosystem.
FAQs
01 What is the potential for the India Cybersecurity Market?
India’s cybersecurity market shows strong potential as enterprises and public agencies harden defenses across cloud, data, identity, and OT/ICS environments. Mandatory obligations (CERT-In incident reporting, DPDP safeguards), rapid digitization of finance, healthcare, and citizen services, and expanding 5G/connectivity are pushing adoption of zero-trust, SASE/SSE, XDR, CNAPP, and MDR/SOC-as-a-Service. The opportunity spans platform suites and managed services, with BFSI, government, IT/ITeS, healthcare, telecom, and manufacturing leading multi-year programs for prevention, detection, and response.
02 Who are the Key Players in the India Cybersecurity Market?
Leading participants include Palo Alto Networks, Cisco Security, Fortinet, Check Point, CrowdStrike, Zscaler, Microsoft Security, IBM Security, Trend Micro, Sophos, Trellix, Tenable, Rapid7, Quick Heal (Seqrite), and Safe Security. These firms dominate due to platform breadth (network, endpoint, cloud, identity, data), strong India partner ecosystems and SOC footprints, deep BFSI and public-sector references, and alignment with compliance requirements (CERT-In directions, DPDP readiness, sectoral norms).
03 What are the Growth Drivers for the India Cybersecurity Market?
Key drivers are (a) regulatory enforcement—CERT-In’s 6-hour incident reporting, log retention, and time-sync mandates alongside the DPDP Act’s penalties catalyze investments; (b) ubiquitous digitization—cloud migration, API-first applications, UPI-scale transactions, and 5G/edge connectivity expand the attack surface; and (c) board-level risk management—ransomware, BEC, and data exfiltration elevate demand for zero-trust architectures, XDR/SIEM-SOAR, identity and data security, and managed detection/response with measurable MTTD/MTTR improvements.
04 What are the Challenges in the India Cybersecurity Market?
Major challenges include (a) skills and capacity gaps—acute scarcity of experienced SOC, DFIR, and cloud security talent; (b) legacy and fragmentation—heterogeneous tech stacks across IT/OT, shadow IT, and tool sprawl complicate integration and continuous compliance; and (c) third-party and MSME exposure—large enterprises depend on suppliers lacking mature controls, raising ecosystem risk and compliance burden; simultaneously, audit bandwidth and continuous assurance remain stretched, demanding automation and year-round readiness.